Introduction
In today’s digital world, security is a top concern for individuals and organizations alike. As more and more sensitive information is stored online, the need for strong and secure authentication methods has never been greater. Passwords have long been the standard for securing online accounts, but they are no longer enough. That’s why the concept of passwordless login is gaining popularity.
I. What is Passwordless Login?
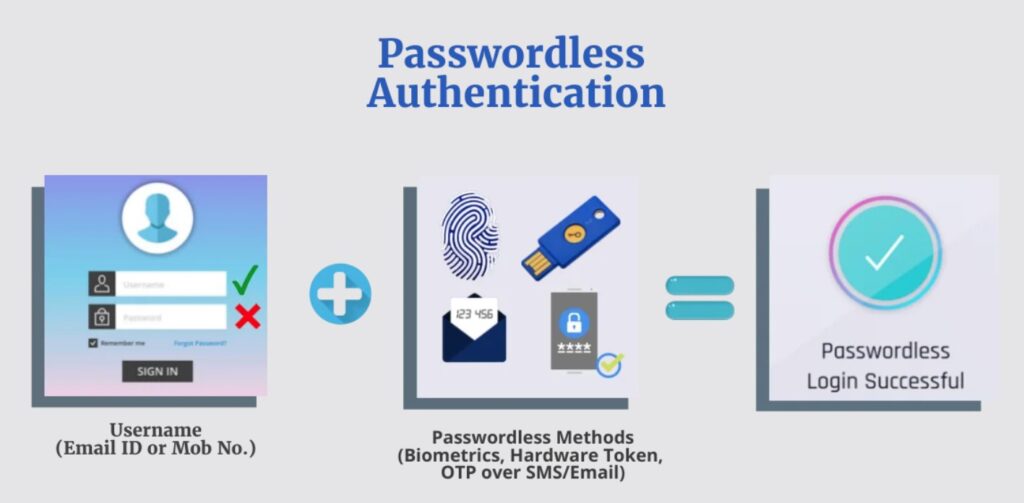
Passwordless login is a method of authentication that eliminates the need for users to remember and enter passwords. Instead of relying on a password, passwordless login uses alternative methods such as biometrics, one-time codes sent via SMS or email, or cryptographic protocols to verify the user’s identity and grant access to the system.
II. Why is Passwordless Login Gaining Popularity?
There are several reasons why passwordless login is becoming more widely adopted. Here are just a few:
1. Increased Security:
Passwords can be easily forgotten or lost, making them an insecure form of authentication. Passwordless login eliminates this vulnerability by relying on something the user has (e.g. a phone or email) instead of something the user knows (e.g. a password).
2. Improved User Experience:
Passwordless login is faster and more convenient than traditional password login. Users don’t have to remember and enter passwords, which can save time and reduce frustration.
3. Reduced Support Costs:
When users forget or lose their passwords, they often have to reset them, which can be a time-consuming and expensive process for organizations. With passwordless login, this issue is eliminated, reducing support costs and improving efficiency.
4. Growing Adoption:
More and more organizations are recognizing the benefits of passwordless login and are adopting it as their preferred method of authentication. This increased adoption has led to the development of more sophisticated and secure passwordless solutions.
III. Types of Passwordless Authentication
There are several types of passwordless authentication, including biometric authentication, SMS authentication, email authentication, and push notifications.
- Biometric authentication uses biometric features, such as facial recognition or fingerprint recognition, to verify a user’s identity. This type of authentication is secure and convenient, as biometric features are unique to each individual and cannot be easily duplicated.
- SMS authentication involves sending a one-time code to the user’s mobile phone, which the user can then use to verify their identity.
- Email authentication works similarly to SMS authentication, except the one-time code is sent to the user’s email address.
- Push notifications are a type of passwordless authentication that can be used on mobile devices. A notification is sent to the user’s device, and the user can use the notification to verify their identity.
IV. Steps for Implementing Passwordless Login:
1. Assess Your Needs:
Evaluate your organization’s authentication needs and determine which passwordless solutions are best suited to meet those needs.
2. Choose a Solution:
Select a passwordless solution that meets your needs and is compatible with your existing systems.
3. Test and Evaluate:
Test the selected solution to ensure it works as expected and evaluate its performance and security.
4. Deploy and Train:
Deploy the passwordless solution and provide training and support to users to help them get started.
5. Monitor and Improve:
Monitor the performance and security of the passwordless solution and make improvements as needed.
V. Challenges in Implementing Passwordless Authentication:
1. Compatibility:
Not all systems and applications support passwordless authentication, so compatibility is a consideration.
2. User Adoption:
Some users may be resistant to change, so user adoption may be a challenge.
3. Security Concerns:
While passwordless authentication is generally more secure than traditional authentication methods, there are security concerns, such as the security of biometric data or security keys.
4. Backup Options:
Passwordless authentication eliminates the need for passwords, so backup options must be in place in case users forget their biometrics or lose their security keys.
5. Costs:
Implementing a passwordless solution can be more expensive than traditional authentication methods, so costs must be carefully evaluated and budgeted for.
VI. Comparing Passwordless Authentication Methods:
1. Biometric authentication:
Biometric authentication uses fingerprints, facial recognition, iris scanning, or other biometric data to authenticate users. It is fast and convenient, but there may be privacy concerns around storing biometric data.
2. Security Keys:
Security keys, such as USB keys or NFC-enabled devices, can be used to authenticate users without a password. They offer strong security, but they can be lost or damaged.
3. One-Time Passcodes:
One-time passcodes can be sent via SMS, email, or an app to authenticate users. They are convenient, but they may not be as secure as other forms of passwordless authentication.
4. Push Notifications:
Push notifications can be sent to users’ smartphones to authenticate them. They are convenient, but may not be as secure as other forms of passwordless authentication.
5. Mobile App-based Authentication:
Mobile apps can be used to authenticate users, either through biometric authentication or by generating one-time passcodes. They offer convenience and security, but users must have a compatible smartphone or device.
6. FIDO2:
The Fast IDentity Online (FIDO) Alliance provides the FIDO2 standard, which provides an open, scalable, and interoperable set of protocols for passwordless authentication. FIDO2-compliant devices can be used with a variety of systems and applications.
Each of these solutions has its own advantages and disadvantages, and organizations must carefully evaluate their needs and requirements before choosing a passwordless authentication solution. Factors such as security, user adoption, compatibility, costs, and backup options should all be considered when making a decision.
VII. List of companies that provide passwordless login solutions:
1. Auth0:
Auth0 provides a universal authentication and authorization platform that enables organizations to authenticate users without passwords. The platform supports a variety of authentication methods, including biometrics, security keys, and push notifications.
2. Okta:
Okta provides a cloud-based identity and access management solution that enables organizations to authenticate users without passwords. The platform supports a variety of authentication methods, including biometrics, security keys, and push notifications.
3. Microsoft:
Microsoft provides a range of passwordless authentication solutions, including Windows Hello for Business, which uses biometrics or security keys to authenticate users, and Microsoft Authenticator, which generates one-time passcodes for authentication.
4. Google:
Google provides a range of passwordless authentication solutions, including Google Smart Lock for Passwords, which automatically signs users in to their accounts on compatible devices, and Google Authenticator, which generates one-time passcodes for authentication.
5. Yubico:
Yubico provides a range of security keys for passwordless authentication, including the YubiKey and the YubiKey 5Ci, which can be used with a variety of systems and applications.
6. RSA:
RSA provides a range of identity and access management solutions, including RSA SecurID, which generates one-time passcodes for authentication.
7. LastPass:
LastPass provides a password management solution that can be used for passwordless authentication, using security keys or biometric authentication to authenticate users.
8. Duo Security:
Duo Security provides a two-factor authentication solution that enables organizations to authenticate users without passwords. The platform supports a variety of authentication methods, including biometrics, security keys, and push notifications.
VIII. Cost of Implementing a Passwordless Login Solution: Factors and Considerations
- The estimated cost of implementing a passwordless login solution in an organization depends on several factors, such as the size of the organization, the number of users, the complexity of the solution, the level of security required, and the method of implementation (in-house or cloud-based).
- For a small organization, the cost of implementing a passwordless login solution could range from a few thousand dollars for a basic, cloud-based solution to tens of thousands of dollars for a more complex, in-house solution. For a larger organization, the cost could be hundreds of thousands of dollars or more.
- Additionally, the cost of implementing a passwordless login solution may also include ongoing expenses, such as licensing fees, support and maintenance costs, and hardware costs (for security keys or other authentication devices).
- In general, the cost of implementing a passwordless login solution should be considered in the context of the overall security and user experience benefits provided by the solution. By eliminating passwords and reducing the risk of security breaches, a passwordless login solution can help organizations to save money and improve their overall security posture.
IX. Conclusion
Passwordless authentication is a secure and convenient alternative to traditional login methods. The future of passwordless authentication looks promising, and organizations that adopt it as part of their security strategy can improve their overall security posture. Despite some challenges and considerations, the benefits of passwordless authentication include improved security, faster authentication, reduced support costs, improved user experience, and increased flexibility. Organizations must carefully evaluate their needs and requirements before implementing a passwordless solution.